Understanding VPN Protocols: A Guide To The Best Protocols
Close to a third (31%) of all internet users rely on virtual private network (VPN) services. If you’re not already among them, you may soon be joining their ranks.
VPNs have rapidly increased in popularity among businesses, as many companies transitioned to remote working environments in 2020. They allow employees and clients to gain remote access to the company’s private network. But VPNs are also well-suited for individual or personal use. Many people already use personal VPNs to help do things like:
- Protect their data when using public wifi
- Stream or download data that may be restricted in their home country
- Hide their browsing activity from their internet service provider (ISP)
But what exactly are VPNs? They help establish a private and secure connection between a public network and a private network. The VPN acts like a tunnel that connects a user from one network to another.
This allows users to send and receive data from the private network. VPNs also hide your internet protocol, or IP address, which makes your internet browsing activity virtually untraceable.
Watch this short youtube video for a primer on all things VPN.
What are VPN protocols?
VPN protocols are specific rules that determine how data is transferred over a VPN. Different protocols may prioritize data transfer speed over data and traffic security and vice versa. Typically, a VPN protocol is either good at prioritizing speed or security—but not often both.
Certain VPN protocols may also be more or less mobile-friendly, which may matter more for personal VPN use.
Generally speaking, VPNs protocols that prioritize security are often better suited for business use cases. VPN protocols that prioritize speed (especially streaming speed) may be better suited for individual or personal use cases.
Watch this YouTube video to learn more about different types of VPN protocols:
6 Common VPN Protocols
Many VPN providers will automatically adjust the VPN protocol to best match your circumstances. If you’re using a VPN to stream videos from another country’s Netflix library, then you probably want to be using a protocol that prioritizes speed over everything else.
But you might find that you want more control over which VPN protocol you’re using at any given time. If so, it’s important to understand the differences between some of the most common VPN protocols. Armed with this knowledge, you can pick the best VPN protocol for your use case.
Below are 6 commonly used VPN protocols, each has its own pros and cons. Use this table as your cheat sheet for figuring out which VPN protocol to use when.
| Protocol | Pros | Cons | Best fit for |
| PPTP | Fast connection speed Easy to set up | Low encryption standard PPTP traffic monitored by the NSA Firewalls can block PPTP | Personal users who want to stream geo-restricted content. Not ideal for users that care about data security. |
| OpenVPN | Transparency from being open-source Highly secure Able to bypass most firewalls | Not easy to manually set up OpenVPN TCP has slower network speeds | Personal users and business users that need a high level of security and decent connection speeds. |
| WireGuard | Transparency from being open-source Easy to set up for an open-source protocol | Newer and not as widely used as some other protocols | Personal users looking for an easy-to-set-up protocol with fast connection speeds. |
| IKEv2/IPSec | Most stable protocol for mobile users Quickly establishes connections Handles network changes well Highly secure | Set up can be difficult Is not supported by many systems or mobile devices | Mobile device users who need to have a stable connection, especially while traveling. |
| SSTP | Integrated with virtually all Microsoft systems Highly secure | Not as transparent as open-source VPN protocols Difficult to set up on non-Windows systems | Ideal for Winders users who place a lot of trust in Microsoft. |
| L2TP/IPSec | More updated than PPTP Highly secure | Not as transparent as open-source VPN protocols Slower VPN connection times Does not handle firewalls well | Ideal for personal users or business users that care about data security. Not ideal for users that need fast connection speeds. |
1. PPTP
Point-to-point tunneling protocol (I.e. PPTP) is one of the oldest VPN protocols still in use. It was originally designed by Microsoft and was integrated into Windows 95. It’s known for having very fast connection speeds, making it ideal for something like streaming video content.
One big downside to point-to-point protocol is that it doesn’t have nearly as many data and traffic security features as other VPN protocols do. It has a low encryption standard that doesn’t make it ideal for use in corporate settings. It also may not be the right choice for personal VPN users that are concerned with data security.
Despite this, PPTP is still commonly built into mobile devices and computers. This makes it one of the easier VPN protocols to set up and start using.
2. OpenVPN
OpenVPN is a popular open-source VPN protocol that was created by James Yonan in 2001. Even though this isn’t always the case with open-source software, OpenVPN is one of the most secure VPN protocols. Anyone can look at the source code to ensure there are no security flaws or vulnerabilities before implementing the protocol.
These two factors (the fact that it’s transparent and highly secure) make it the protocol of choice for many VPN providers around the world. It also helps that the protocol is available on multiple different platforms:
- Windows
- Mac
- Android
- iOS
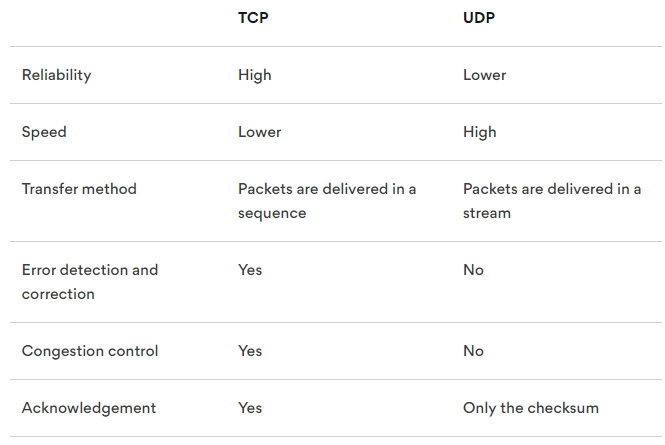
There are two main types of OpenVPN: transmission control protocol (TCP) and user datagram protocol (UDP). TCP prioritizes reliability and sends data packets in a specific sequence, though this can also slow down network speeds. On the other hand, UDP sends data in a continuous stream rather than individually sequences packets, thereby prioritizing speed over data security.
Here’s a quick explainer on some of the other differences between OpenVPN TCP vs. UDP:
3. WireGuard
WireGuard is a relatively new VPN protocol. It was designed to replace another VPN protocol: IPSec. Overall, it’s meant to be a lightweight protocol that is fast and secure.
Like OpenVPN, WireGuard is also open-source, giving the protocol extra transparency. One key difference between OpenVPN and WireGuard is that WireGuard is a lot easier to set up. Since it’s a newer VPN protocol, Wireguard benefits from things like a more up-to-date encryption standard, faster connection times, and increased reliability.
It is also available on multiple platforms including:
- Windows
- Mac
- Android
- iOS
However, there is a caveat to be aware of. As a newer open-source protocol, not all VPN providers have added WireGuard to the line-up of protocols they offer users. If you’re interested in using the WireGuard protocol, double-check that your VPN provider offers it first.
4. IKEv2/IPSec
The internet key exchange version 2 (or IKEv2) was jointly designed by Microsoft and Cisco. On its own, IKEv2 is simply a tunneling protocol that provides a secure key exchange session. I.e. it doesn’t have built-in data encryption. For this reason, it’s frequently paired with IPSec, which provides the data encryption and authentication piece. IPSec stands for internet security protocol.
As a VPN protocol, IKEv2 & IPSec is great at reconnecting users to the network when a connection is dropped. It’s also ideal for mobile device users, especially 3G or 4G LTE devices. So if you travel frequently and rely on your mobile device to connect to networks while traveling, this protocol may be the right one for you.
One drawback of using IKEv2/IPSec is that it’s not as widely used as other VPN protocols. It’s not easily implemented on all computer and mobile device systems.
5. SSTP
Secure socket tunneling protocol (SSTP) might be the best (or at least most user-friendly) VPN protocol for Microsoft users. It comes fully integrated with all Microsoft operating systems (since Windows Vista).
The fact that SSTP is a proprietary Microsoft protocol has a few consequences. On the one hand, it’s not an open-source protocol where anyone can look under the hood to audit the source code. Yet most users still say it is a fairly secure VPN protocol.
It has built-in support for Linux, Windows, and BSD systems. Android, macOS, and iOS users will have to find support through third-party clients. Overall, SSTP is likely only well-suited for Windows users that trust the Microsoft brand name.
6. L2TP/IPSec
Layer 2 Tunnel Protocol (L2TP) is the next generation of PPTP. It combines PPTP with L2F (Layer 2 Forwarding Protocol) that was designed by Cisco.
L2TP is decently popular among VPN service providers and users. It’s more secure than the older PPTP and provides users with more features as well.
Just like IKEv2, L2TP doesn’t offer any data encryption or authentication by itself. It is usually paired with IPSec, which provides this functionality. One helpful thing to note about IPSec is that it secures and encrypts data to military standards. This may be especially attractive for users that are concerned with data privacy.
One downside is that the extra layer of security from IPSec can slow down computer processing times, resulting in a slower connection. L2TP/IPSec also doesn’t handle getting around firewalls well.
Which VPN Protocol is Right for You?
While there are multiple other VPN protocols out there, the 6 protocols are the ones you’ll run into most often.
In terms of figuring out which VPN protocol to use in any given situation, there are 3 key factors to keep in mind:
Ease of use
Some VPN protocols are easier to set up than others. For example, PPTP is known for being easy to set up. SSTP also comes integrated with almost all Microsoft devices. On the other hand, Open VPN and IKEv2/IPSec can be more difficult to set up yourself.
If you need a VPN protocol you can set up and start using right away, consider using PPTP or SSTP.
Security and privacy
Many VPN protocols either handle data encryption & authentication or connection speed, but rarely both. Some newer VPN protocols like WireGuard aim to offer users both. But many others lean either towards security or speed. When thinking about what type of VPN protocol to use, ask yourself if data security or connection speed matters more.
If security matters more to you or your organization, consider using OpenVPN, IKEv2/IPSec, or L2TP/IPSec. Conversely, if you mainly care about data transfer and connection speed, a protocol like PPTP may work better for you.
Speed
Connection speed is the other side of the data security coin. VPN protocols with the highest level of data encryption and security often have slower network speeds. For personal or business users that may be sharing sensitive information, this is well worth the trade-off.
But if you plan on using a personal VPN to do things like consume geo-restricted content, a protocol like PPTP might be ideal. PPTP prioritizes speed over data security, which makes for a great video streaming experience.
Visit the TrustRadius VPN Solutions page to learn more about how VPN software works.
Was this helpful?

Want to learn more about VPN solutions, view products, and read real reviews? Check out our category page here!