Trellix Endpoint Security ENSFormerly FireEye +McAfee Endpoint Security
Overview
What is Trellix Endpoint Security ENS?
Trellix Endpoint Security (ENS) solutions apply proactive threat intelligence and defenses across the entire attack lifecycle to keep organizations safer and more resilient.
Recent Reviews
Popular Features
- Centralized Management (14)9.090%
- Malware Detection (14)9.090%
- Infection Remediation (13)8.080%
- Endpoint Detection and Response (EDR) (13)8.080%
Reviewer Pros & Cons
Pricing
Entry-level set up fee?
- No setup fee
Offerings
- Free Trial
- Free/Freemium Version
- Premium Consulting/Integration Services
Would you like us to let the vendor know that you want pricing?
130 people also want pricing
Alternatives Pricing
Features
Return to navigation
Product Details
- About
- Competitors
- Tech Details
- Downloadables
- FAQs
What is Trellix Endpoint Security ENS?
Trellix Endpoint Security (ENS) solutions apply proactive threat intelligence and defenses across the entire attack lifecycle to keep organizations safer and more resilient.
Endpoint Security
Provides intelligent endpoint security that aligns to the organization's prioritized security needs—from preventing and hunting threats to tailoring security controls.
Endpoint Detection and Response
An advanced EDR solution helps users to reduce alert noise and empower analysts to reduce mean time to detect and respond to threats through automation.
Endpoint Security
Provides intelligent endpoint security that aligns to the organization's prioritized security needs—from preventing and hunting threats to tailoring security controls.
Endpoint Detection and Response
An advanced EDR solution helps users to reduce alert noise and empower analysts to reduce mean time to detect and respond to threats through automation.
Endpoint Forensics
Remotely detect and investigate endpoint cyberattacks including hidden malware. Automate triage with other sources to determine root case and resolve the incident.
Trellix Connect
Trellix Connect
Fast track SIEM workflows and outcomes with expert-built ready to deploy content packs for connecting, monitoring, and automating security operations.
Trellix Endpoint Security ENS Features
Endpoint Security Features
- Supported: Anti-Exploit Technology
- Supported: Endpoint Detection and Response (EDR)
- Supported: Centralized Management
- Supported: Infection Remediation
- Supported: Vulnerability Management
- Supported: Malware Detection
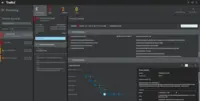
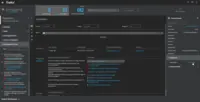
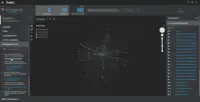
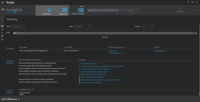
Trellix Endpoint Security ENS Screenshots
Trellix Endpoint Security ENS Video
Protect and empower your workforce with an integrated security framework that protects every endpoint. Trellix Endpoint Security (ENS) solutions apply proactive threat intelligence and defenses across the entire attack lifecycle to keep your organization safer and more resilient.
Trellix Endpoint Security ENS Competitors
Trellix Endpoint Security ENS Technical Details
| Deployment Types | Software as a Service (SaaS), Cloud, or Web-Based |
|---|---|
| Operating Systems | Unspecified |
| Mobile Application | No |
Trellix Endpoint Security ENS Downloadables
Frequently Asked Questions
Trellix Endpoint Security (ENS) solutions apply proactive threat intelligence and defenses across the entire attack lifecycle to keep organizations safer and more resilient.
Symantec Endpoint Security, CrowdStrike Falcon, and Watchguard Endpoint Security are common alternatives for Trellix Endpoint Security ENS.
Reviewers rate Centralized Management and Malware Detection highest, with a score of 9.
The most common users of Trellix Endpoint Security ENS are from Enterprises (1,001+ employees).