IBM Security QRadar SOAR
Overview
What is IBM Security QRadar SOAR?
IBM Security® QRadar® SOAR is designed to help your security team respond to cyberthreats with confidence, automate with intelligence and collaborate with consistency. It guides your team in resolving incidents by codifying established incident response processes into dynamic playbooks.
Recent Reviews
Awards
Products that are considered exceptional by their customers based on a variety of criteria win TrustRadius awards. Learn more about the types of TrustRadius awards to make the best purchase decision. More about TrustRadius Awards
Reviewer Pros & Cons
Pricing
Entry-level set up fee?
- No setup fee
For the latest information on pricing, visithttps://www.ibm.com/products/qradar…
Offerings
- Free Trial
- Free/Freemium Version
- Premium Consulting/Integration Services
Would you like us to let the vendor know that you want pricing?
22 people also want pricing
Alternatives Pricing
Product Demos
Accelerating Response Time with IBM Security QRadar
mediacenter.ibm.com
IBM Security QRadar SOAR demo
mediacenter.ibm.com
Product Details
- About
- Integrations
- Competitors
- Tech Details
- Downloadables
- FAQs
What is IBM Security QRadar SOAR?
IBM Security® QRadar® SOAR is designed to improve SOC efficiency and ensure users' response processes are met with an intelligent automation and orchestration solution, which timestamps key actions, aides threat investigation, and helps users manage their response to 180+ international privacy and data breach regulations. It features prebuilt connectors for a broad ecosystem of connectors, while managing the organization's response.
- Respond and Remediate Faster – using open standards ingest alerts from disparate data sources into a unified dashboard for improved investigation and response across the security, IT and other key stakeholders.
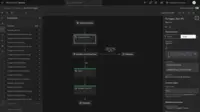
- Customized Case Management – pre-built playbooks that adapt to any unique business processes using customizable layouts and tailored response. This facilitates getting started quicker, reduces complexity, and helps improve the incident response process.
- Close the Skill Gap – create automations that bring together artifact correlation, threat enrichment, case investigation, and prioritization so analysts can process triaged cases faster. The playbook evolves as the investigation proceeds, with threat enrichment happening at each stage of the process.
IBM Security QRadar SOAR Features
- Supported: Case management
- Supported: Dynamic playbooks
- Supported: Integrations out of the box
- Supported: Deployment flexibility
- Supported: Visual workflow
- Supported: Privacy breach response
- Supported: Automation
IBM Security QRadar SOAR Screenshots
IBM Security QRadar SOAR Video
IBM Security QRadar SOAR Integrations
IBM Security QRadar SOAR Competitors
IBM Security QRadar SOAR Technical Details
| Deployment Types | On-premise, Software as a Service (SaaS), Cloud, or Web-Based |
|---|---|
| Operating Systems | Windows, Linux, Mac |
| Mobile Application | No |
IBM Security QRadar SOAR Downloadables
Frequently Asked Questions
IBM Security® QRadar® SOAR is designed to help your security team respond to cyberthreats with confidence, automate with intelligence and collaborate with consistency. It guides your team in resolving incidents by codifying established incident response processes into dynamic playbooks.
Palo Alto Networks Cortex XSOAR, FortiSOAR, and Splunk SOAR are common alternatives for IBM Security QRadar SOAR.
The most common users of IBM Security QRadar SOAR are from Enterprises (1,001+ employees).