Overview
What is IBM Security QRadar EDR?
IBM Security QRadar EDR (formerly ReaQta) combines automation and dashboards to minimize analyst workloads, detect anomalous endpoint behavior and remediate threats in near real time.With visibility across endpoints, it combines expected features, like MITRE ATT&CK mapping and attack visualizations, with…
How IBM Security QRadar EDR Differs From Its Competitors
Awards
Products that are considered exceptional by their customers based on a variety of criteria win TrustRadius awards. Learn more about the types of TrustRadius awards to make the best purchase decision. More about TrustRadius Awards
Popular Features
- Endpoint Detection and Response (EDR) (9)8.585%
- Centralized Management (9)8.383%
- Malware Detection (9)8.383%
- Infection Remediation (9)8.181%
Reviewer Pros & Cons
- Its interface & robust search capabilities analysts easily conduct detailed investigations & uncover IOCs as well as suspicious patterns of behavior.
- QRadar EDR gives many predefined detection rules & response actions but from our team member found out limitations in terms of customization & flexibi...
Pricing
Entry-level set up fee?
- Setup fee optional
Offerings
- Free Trial
- Free/Freemium Version
- Premium Consulting/Integration Services
Would you like us to let the vendor know that you want pricing?
8 people also want pricing
Alternatives Pricing
Features
Product Details
- About
- Integrations
- Competitors
- Tech Details
- Downloadables
- FAQs
What is IBM Security QRadar EDR?
IBM Security QRadar EDR (formerly ReaQta) combines automation and dashboards to minimize analyst workloads, detect anomalous endpoint behavior and remediate threats in near real time.
With visibility across endpoints, it combines expected features, like MITRE ATT&CK mapping and attack visualizations, with dual-engine AI and automation.
For teams that need extended support, managed detection and response (MDR) services offers 24/7 monitoring and response to help keep users protected. QRadar EDR can be deployed as SaaS, on-premises and in air-gapped environments.
https://ibm.biz/QRadar_EDR_product_page
IBM Security QRadar EDR Features
Endpoint Security Features
- Supported: Anti-Exploit Technology
- Supported: Endpoint Detection and Response (EDR)
- Supported: Centralized Management
- Supported: Hybrid Deployment Support
- Supported: Infection Remediation
- Supported: Malware Detection
Additional Features
- Supported: Pre-execution prevention: Reviews file source code prior to full execution and stop files from running if malicious code is detected.
- Supported: NanoOS: Each endpoint agent includes dual AI engines and NanoOS technology, which allows certain detection and autonomous operation capabilities even when endpoints are offline.
- Supported: Attack visibility: Detects and correlates alert information, including an attack’s root cause, risk assessment, and MITRE ATT&CK framework.
- Supported: Anti-ransomware: Analyzes file behaviors for detecting imminent attacks and stop malicious processes from executing.
- Supported: Signature scanning: Uses heuristics and signature-based prevention.
- Supported: Threat insights: Identifies potential threats with metadata-based analysis to expedite triaging and enable detection of an alert’s artifacts to discover new binaries as soon as they’re activated.
- Supported: AI-driven Threat hunting: Enables real-time search for indicators of compromise (IOC), binaries and behaviors to facilitate the discovery of dormant threats.
- Supported: Forensics: Enables remote gathering of forensic information to reconstruct an attacker’s activities.
- Supported: Custom playbook: Creates custom-built detection response and remediation playbooks.
- Supported: API access: Automates workflows and integrate with external platforms with Direct API access to ReaQta.
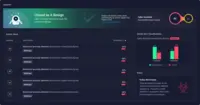
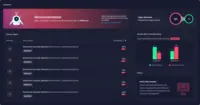
IBM Security QRadar EDR Screenshots
IBM Security QRadar EDR Videos
Watch 2-minute demo video
Watch 2-minute explainer video
IBM Security QRadar EDR Integrations
IBM Security QRadar EDR Competitors
IBM Security QRadar EDR Technical Details
| Deployment Types | Software as a Service (SaaS), Cloud, or Web-Based |
|---|---|
| Operating Systems | Unspecified |
| Mobile Application | No |
| Supported Countries | Global |
| Supported Languages | English |