1touch.io vs. SecuPi
1touch.io vs. SecuPi
| Product | Rating | Most Used By | Product Summary | Starting Price |
|---|---|---|---|---|
1touch.io | N/A | 1touch.io, from the company of the same name in Stamford, discovers, maps, and tracks personal data in the enterprise network, using unique and proprietary network analytics. This is done for structured and unstructured data, known and unknown data, and for data in rest and in motion. The vendor states their goal is data security and privacy, and to provide stakeholders a holistic view of how data stored, processed and shared. | N/A | |
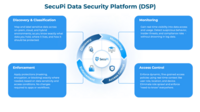
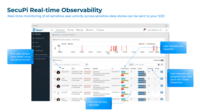
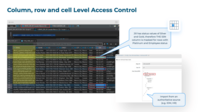
SecuPi | N/A | SecuPi helps enterprises protect and take control of their data, ensuring it is discovered, monitored, governed, and secured in a compliant way. The SecuPi Data Security Platform gives organizations clarity into where sensitive data lives, who is accessing it, and how it is being used. By unifying discovery, monitoring, access control, and enforcement into one consistent approach, SecuPi embeds security directly into business applications, analytics, cloud platforms, and AI workloads, so data… | N/A |
| 1touch.io | SecuPi | |||||||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| Editions & Modules | No answers on this topic | No answers on this topic | ||||||||||||||
| Offerings |
| |||||||||||||||
| Entry-level Setup Fee | No setup fee | No setup fee | ||||||||||||||
| Additional Details | — | — | ||||||||||||||
| More Pricing Information | ||||||||||||||||
| 1touch.io | SecuPi | |
|---|---|---|
| ScreenShots | SecuPi Screenshots |