BlackNoise vs. Blue Lava
BlackNoise vs. Blue Lava
| Product | Rating | Most Used By | Product Summary | Starting Price |
|---|---|---|---|---|
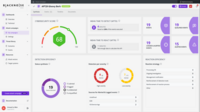
BlackNoise | Enterprise companies (1,001+ employees) | BlackNoise is a solution that provides proof of cyber defense effectiveness. A European cyber defense validation platform, it helps users across all industries to continuously validate and enhance cyber defense capabilities against advanced threats, including APTs, ransomware, and state-sponsored attacks. By delivering real-world performance metrics, it enables precise tracking and improvement of Mean Time to Detect and Respond (MTTD/R), offering visibility into critical KPIs to support… | N/A | |
Blue Lava | N/A | Blue Lava offers a technology solution to evaluate an organization's security investment, used to perform on-demand, in-depth risk assessments mapping to security maturity, NIST, other key frameworks, and peer benchmarking or to prioritize, plan, and execute security program improvements to align with business objectives and risk appetite. | N/A |
| BlackNoise | Blue Lava | |||||||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| Editions & Modules | No answers on this topic | No answers on this topic | ||||||||||||||
| Offerings |
| |||||||||||||||
| Entry-level Setup Fee | No setup fee | No setup fee | ||||||||||||||
| Additional Details | — | — | ||||||||||||||
| More Pricing Information | ||||||||||||||||
| BlackNoise | Blue Lava | |
|---|---|---|
| Small Businesses | No answers on this topic | No answers on this topic |
| Medium-sized Companies | Microsoft Defender for Cloud Score 8.4 out of 10 | Microsoft Defender for Cloud Score 8.4 out of 10 |
| Enterprises | Microsoft Defender for Cloud Score 8.4 out of 10 | Microsoft Defender for Cloud Score 8.4 out of 10 |
| All Alternatives | View all alternatives | View all alternatives |
| BlackNoise | Blue Lava | |
|---|---|---|
| ScreenShots | BlackNoise Screenshots |