Overview
What is Xygeni?
End to end Software Supply Chain Security. Xygeni shields the Software Supply Chain from unseen threats, providing comprehensive visibility and control throughout the entire SDLC. The platform enables systematic risk assessment, prioritizes threatened components, and enhances the organization's global security posture. …
Recent Reviews

Leaving a review helps other professionals like you evaluate Application Security Tools
Be the first one in your network to review Xygeni, and make your voice heard!
Get StartedPricing
Entry-level set up fee?
- No setup fee
Offerings
- Free Trial
- Free/Freemium Version
- Premium Consulting/Integration Services
Would you like us to let the vendor know that you want pricing?
Alternatives Pricing
Product Details
- About
- Competitors
- Tech Details
What is Xygeni?
End to end Software Supply Chain Security.
Xygeni shields the Software Supply Chain from unseen threats, providing comprehensive visibility and control throughout the entire SDLC. The platform enables systematic risk assessment, prioritizes threatened components, and enhances the organization's global security posture.
Xygeni Products:
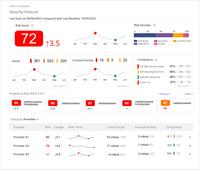
- Security Posture: Continuous monitoring, assessment, and management of the security risks within the pipeline, infrastructure, and teams
- SDLC Inventory: Discovers and catalogs all artifacts, resources, and dependencies by their security posture.
- CI/CD Security: Prevents insecure configuration and ensures the end-to-end software supply chain remains steadfastly secure.
- Build Security: Xygeni's attestation ensures no unauthorized changes have taken place in CI/CD processes.
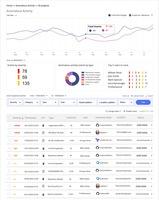
- Anomaly Detection: Real-time detection and alerting of anomalous activity that may cause or be a precursor to an attack.
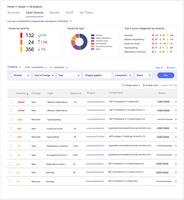
- Open Source Security & SBOM: Identifies questionable dependencies and malicious code that may compromise software projects.
- Secrets Security: Identifies secrets throughout the entire SDLC and prevent new secrets included in coding, building, and delivery actions
- IaC Security: Ensures security and integrity of IaC templates to avoid replicating vulnerabilities at scale
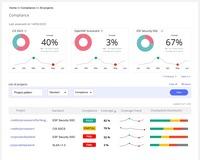
- Compliance: Enforces and provides evidence that security policies are applied throughout all stages of the SDLC.
Xygeni’s capabilities provide complete visibility in the software supply chain, enabling a systematic process for assessing the risks associated with the Software Supply Chain, identifying and prioritizing the most critical components, and evaluating and improving their global and detailed security posture.
Ultimately, Xygeni is used to protect the integrity and security of software assets, pipelines and infrastructure of the entire Software Supply Chain.
Xygeni shields the Software Supply Chain from unseen threats, providing comprehensive visibility and control throughout the entire SDLC. The platform enables systematic risk assessment, prioritizes threatened components, and enhances the organization's global security posture.
Xygeni Products:
- Security Posture: Continuous monitoring, assessment, and management of the security risks within the pipeline, infrastructure, and teams
- SDLC Inventory: Discovers and catalogs all artifacts, resources, and dependencies by their security posture.
- CI/CD Security: Prevents insecure configuration and ensures the end-to-end software supply chain remains steadfastly secure.
- Build Security: Xygeni's attestation ensures no unauthorized changes have taken place in CI/CD processes.
- Anomaly Detection: Real-time detection and alerting of anomalous activity that may cause or be a precursor to an attack.
- Open Source Security & SBOM: Identifies questionable dependencies and malicious code that may compromise software projects.
- Secrets Security: Identifies secrets throughout the entire SDLC and prevent new secrets included in coding, building, and delivery actions
- IaC Security: Ensures security and integrity of IaC templates to avoid replicating vulnerabilities at scale
- Compliance: Enforces and provides evidence that security policies are applied throughout all stages of the SDLC.
Xygeni’s capabilities provide complete visibility in the software supply chain, enabling a systematic process for assessing the risks associated with the Software Supply Chain, identifying and prioritizing the most critical components, and evaluating and improving their global and detailed security posture.
Ultimately, Xygeni is used to protect the integrity and security of software assets, pipelines and infrastructure of the entire Software Supply Chain.
Xygeni Features
- Supported: Full Visibility & Control
- Supported: Ever-Vigilant Scanning Strategy
- Supported: Unified CI/CD Control Plane
- Supported: Security Posture Trends And Reporting
- Supported: Prevention & Remediation
- Supported: Attack Detection
- Supported: Continuous Compliance & SBOM
Xygeni Screenshots
Xygeni Competitors
Xygeni Technical Details
| Deployment Types | Software as a Service (SaaS), Cloud, or Web-Based |
|---|---|
| Operating Systems | Unspecified |
| Mobile Application | No |
| Supported Countries | Global |
| Supported Languages | English |