SoftActivity vs. Syteca
SoftActivity vs. Syteca
| Product | Rating | Most Used By | Product Summary | Starting Price |
|---|---|---|---|---|
SoftActivity | N/A | Deep Software in North Vancouver is a security software company that develops and provides SoftActivity, a user monitoring software for companies and organizations to monitor their employee's computer usage. SoftActivity helps to protect companies from insider threats, IP theft, fraudulent activity by employees and improve staff productivity. | N/A | |
Syteca | N/A | Syteca is a cybersecurity platform for organizations looking to safeguard their critical systems and information against internal threats. With customizable privileged access management (PAM) and user activity monitoring (UAM), Syteca empowers businesses to protect their most critical assets. Whether securing sensitive information through advanced privilege controls or gaining complete visibility into user activity, Syteca aims to ensure robust internal protection. Syteca is… | N/A |
| SoftActivity | Syteca | |||||||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| Editions & Modules | No answers on this topic | No answers on this topic | ||||||||||||||
| Offerings |
| |||||||||||||||
| Entry-level Setup Fee | No setup fee | No setup fee | ||||||||||||||
| Additional Details | — | — | ||||||||||||||
| More Pricing Information | ||||||||||||||||
| SoftActivity | Syteca | |
|---|---|---|
| Small Businesses | No answers on this topic | No answers on this topic |
| Medium-sized Companies | ManageEngine ADAudit Plus Score 9.1 out of 10 | ManageEngine ADAudit Plus Score 9.1 out of 10 |
| Enterprises | ManageEngine ADAudit Plus Score 9.1 out of 10 | ManageEngine ADAudit Plus Score 9.1 out of 10 |
| All Alternatives | View all alternatives | View all alternatives |
| SoftActivity | Syteca | |
|---|---|---|
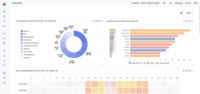
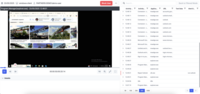
| ScreenShots | Syteca Screenshots |