Overview
What is SearchInform FileAuditor?
SearchInform FileAuditor is a DCAP solution (data-centric audit and protection) for automated audit of information storages, search for access violations and tracking changes made to critical data. The system protects confidential documents from careless and deliberate malicious actions of employees and puts…

Leaving a review helps other professionals like you evaluate Data-Centric Audit Protection (DCAP) Software
Be the first one in your network to review SearchInform FileAuditor, and make your voice heard!
Get StartedProduct Details
- About
- Competitors
- Tech Details
What is SearchInform FileAuditor?
SearchInform FileAuditor is a DCAP solution (data-centric audit and protection) for automated audit of information storages, search for access violations and tracking changes made to critical data. The system protects confidential documents from careless and deliberate malicious actions of employees and puts things in order in file storages.
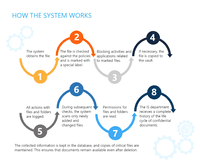
How FileAuditor solves the problem of monitoring the security of critical data:
· Classification of vulnerable data
Finds files in a document flow that contain critical information, and adds a special mark to each file, indicating the type of info it contains: personal data, trade secret, credit card numbers, etc.
· Access rights audit
Controls access rights to information (full access, editing, reading, writing, reading and changing, etc.). Tracks employees who have unauthorized access to data. Finds confidential files stored in violation of established security rules (in the public domain, in shared network folders, on employee PCs, etc.)
· Monitoring and blocking user actions
Audits user operations with the file system. The responsible person is always aware of up-to-date information on the lifecycle of a file (creation, editing, transfer, deletion, etc.). Blocks access to the file and its transfer in any application.
· Critical documents archiving
Makes shadow copies of critical files found on a PC, server or in network folders, saves the history of their revisions. Confidential data archive helps in incident investigation and ensures recovery of lost information.
ADVANTAGES
· PC load control and memory saving – monitoring can be scheduled or provoked by a particular event or condition; it's possible to keep only sensitive documents; a deduplication system saves storage space
· Ability to deploy and operate the software in the cloud. The software can be deployed in the cloud, which allows companies that do not have their own IT infrastructure to use the system.
· Due to customizable rule settings specialists don't have to deal with unnecessary tasks and can focus on monitoring only critical data.
· Changes made to files can be tracked almost instantly – the system saves a specified number of file revisions which helps during internal investigation
· Proactive protection of files from changes and transfers. The system can be configured to block access to documents to prevent unwanted user actions with the files.
· Seamless integration with Risk Monitor or DLP extends the functionality of the solution
SearchInform FileAuditor Features
- Supported: Classification of vulnerable data
- Supported: Access rights audit
- Supported: Critical documents archiving
- Supported: User activity monitoring
SearchInform FileAuditor Screenshots
SearchInform FileAuditor Competitors
SearchInform FileAuditor Technical Details
| Deployment Types | On-premise, Software as a Service (SaaS), Cloud, or Web-Based |
|---|---|
| Operating Systems | Windows, Linux |
| Mobile Application | No |
| Supported Countries | Global |
| Supported Languages | English, Spanish, Portuguese, Russian. |