Starting at $17,000 per year per installation
View PricingOverview
What is TheHive?
TheHive is an open source and free cybersecurity incident response platform.
Recent Reviews
Pricing
TheHive Gold Edition
Starting from $17.000
On Premise
per year per installation
TheHive Platinum Edition
Starting from $23.000
On Premise
per year per installation
TheHive Cloud Platform - Large
Starting from $41.000
Cloud
per year per installation
Entry-level set up fee?
- $5,000 one-time fee per installationOptional
For the latest information on pricing, visithttps://www.strangebee.com/thehive/pric…
Offerings
- Free Trial
- Free/Freemium Version
- Premium Consulting/Integration Services
Starting price (does not include set up fee)
- $17,000 per year per installation
Product Details
- About
- Integrations
- Competitors
- Tech Details
- FAQs
What is TheHive?
TheHive was purpose built for SOC, CERT and CSIRT teams to minimize the time between actions taken by a bad actor and a team’s security response unit. Whether the goal is to share observables with a team, open a case, correlate incidents, or automate forensic analysis, TheHive, enables the user to do it.
TheHive Features
Incident Response Platforms Features
- Supported: Company-wide Incident Reporting
- Supported: Integration with Other Security Systems
- Supported: Attack Chain Visualization
- Supported: Centralized Dashboard
- Supported: Live Response for Rapid Remediation
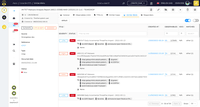
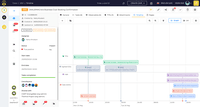
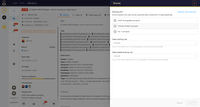
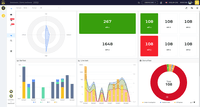
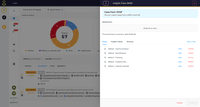
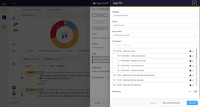
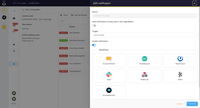
TheHive Screenshots
TheHive Video
TheHive 5 new features
TheHive Integrations
TheHive Technical Details
| Deployment Types | On-premise, Software as a Service (SaaS), Cloud, or Web-Based |
|---|---|
| Operating Systems | Windows, Linux |
| Mobile Application | No |
| Supported Languages | English, French, Italian, German, Dutch, Spanish, Portuguese, Polish, Swedish, Chinese, Japanese, Arabic |
Frequently Asked Questions
TheHive is an open source and free cybersecurity incident response platform.
TheHive starts at $17000.
The most common users of TheHive are from Enterprises (1,001+ employees).
TheHive Customer Size Distribution
| Consumers | 0% |
|---|---|
| Small Businesses (1-50 employees) | 0% |
| Mid-Size Companies (51-500 employees) | 30% |
| Enterprises (more than 500 employees) | 70% |