Microsoft SentinelFormerly Azure Sentinel
Overview
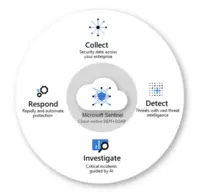
What is Microsoft Sentinel?
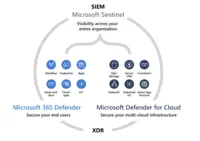
Microsoft Sentinel (formerly Azure Sentinel) is designed as a birds-eye view across the enterprise. It is presented as a security information and event management (SIEM) solution for proactive threat detection, investigation, and response.
Surpassingly really good tool and a very interactive dashboard
SIEM means Sentinel
Why you should start using Microsoft Sentinel today.
Sentinel: Your one stop SIEM for cloud for Bird's Eyes by MS.
Microsoft Sentinel, the scaleable cloud-native SIEM platform
Unleashing the Power of Data for Seamless Security Investigations
Review of Microsoft Sentinel
One stop solution for all security needs. Transforming Security with AI and Automation
Excellent cloud security solution with intelligent analytics and automation offered by Microsoft.
A big SIEM or a little SOAR?
Microsoft Sentinel Review
Microsoft Sentinel Review
Microsoft Sentinel Review
Microsoft Sentinel Review
How Microsoft Sentinel Differs From Its Competitors
Sources
Investigation Tools
Sources
AI and ML
Investigation Tools
Sources
Third party products include Workday, Google Workspaces, …
AI and ML
While I have a very limited experience with using Azure Open AI in the incident through playbooks, it surely …
Investigation Tools
Sources
Investigation Tools
Sources
AI and ML
Investigation Tools
Sources
On-Premises Identity events
Azure platform events
Defender and other Microsoft products
On-premises appliances
Linux events
This same counts towards Azure activity, Azure VMs and …
AI and ML
Next to that we use the Fusion rules that will detect multi-stage attack scenarios
Sentinel notebooks are not used a lot at this moment, because of the learning curve
Investigation Tools
Sources
- Microsoft 365 Services: Data from Microsoft 365 services, including Exchange Online, SharePoint, Teams, and Azure Active Directory, were ingested to monitor email, document, and user activities.
- Azure Services: Data …
AI and ML
Investigation Tools
Impact: Analysts quickly retrieved relevant data, which resulted in reducing the time it takes to gather evidence and establish the scope of …
Sources
AI and ML
Investigation Tools
Sources
AI and ML
Investigation Tools
Sources
AI and ML
Investigation Tools
Sources
Investigation Tools
Sources
Investigation Tools
Sources
AI and ML
Investigation Tools
Sources
AI and ML
Investigation Tools
Sources
Investigation Tools
Awards
Products that are considered exceptional by their customers based on a variety of criteria win TrustRadius awards. Learn more about the types of TrustRadius awards to make the best purchase decision. More about TrustRadius Awards
Popular Features
- Centralized event and log data collection (14)8.686%
- Correlation (14)8.484%
- Event and log normalization/management (14)8.282%
- Custom dashboards and workspaces (14)7.474%
Reviewer Pros & Cons
Pricing
Azure Sentinel
$2.46
100 GB per day
$123.00
200 GB per day
$221.40
Entry-level set up fee?
- No setup fee
Offerings
- Free Trial
- Free/Freemium Version
- Premium Consulting/Integration Services
Product Demos
Microsoft Sentinel: Monitoring health and integrity of analytics rules
Features
Security Information and Event Management (SIEM)
Security Information and Event Management is a category of security software that allows security analysts to look at a more comprehensive view of security logs and events than would be possible by looking at the log files of individual, point security tools
- 8.6Centralized event and log data collection(14) Ratings
Effectiveness of real-time centralized event and log data collection
- 8.4Correlation(14) Ratings
Correlation of logs and events to pinpoint significant threats
- 8.2Event and log normalization/management(14) Ratings
Ability to normalize event syntax so that logs can be compared and are machine-understandable
- 9.2Deployment flexibility(13) Ratings
Ability to tune system to maximize threat detection and minimize false positives
- 8.5Integration with Identity and Access Management Tools(13) Ratings
Integration with access control tools like Active Directory and LDAP
- 7.4Custom dashboards and workspaces(14) Ratings
dashboards that can be customized to meet the needs of specific groups
- 7.6Host and network-based intrusion detection(13) Ratings
Ability to detect both endpoint intrusion and network ingress detection
- 8.2Data integration/API management(14) Ratings
Ease and quality of data integrations between SIEM and other systems
- 8.7Behavioral analytics and baselining(12) Ratings
How effectively activity and behavior baselines are established and maintained
- 8.5Rules-based and algorithmic detection thresholds(13) Ratings
Effectiveness of manually-established rules and algorithmically-determined detection thresholds
- 8.4Response orchestration and automation(14) Ratings
Quality of built-in response orchestration and automation in Next-Gen SIEM
- 9Reporting and compliance management(4) Ratings
Ease and quality of reporting and compliance functions
- 8.6Incident indexing/searching(14) Ratings
Effectiveness of searching across structured and unstructured events and incidents within SIEM
Product Details
- About
- Competitors
- Tech Details
- FAQs
What is Microsoft Sentinel?
Helps users to protect the digital estate: Secures the digital estate with scalable, integrated coverage for a hybrid, multicloud, multiplatform business.
Microsoft intelligence to Empower SOC: Optimizes SecOps with advanced AI, security expertise, and threat intelligence.
Detection, investigation and Response: A unified set of tools to monitor, manage, and respond to incidents.
Cost of ownership: A cloud-native SaaS solution to reduce infrastructural costs.
Microsoft Sentinel Features
Security Information and Event Management (SIEM) Features
- Supported: Centralized event and log data collection
- Supported: Correlation
- Supported: Event and log normalization/management
- Supported: Deployment flexibility
- Supported: Integration with Identity and Access Management Tools
- Supported: Custom dashboards and workspaces
- Supported: Host and network-based intrusion detection
- Supported: Log retention
- Supported: Data integration/API management
- Supported: Behavioral analytics and baselining
- Supported: Rules-based and algorithmic detection thresholds
- Supported: Response orchestration and automation
- Supported: Incident indexing/searching
Microsoft Sentinel Screenshots
Microsoft Sentinel Videos
Microsoft Sentinel Competitors
Microsoft Sentinel Technical Details
| Deployment Types | Software as a Service (SaaS), Cloud, or Web-Based |
|---|---|
| Operating Systems | Unspecified |
| Mobile Application | No |
Frequently Asked Questions
Comparisons
Compare with
Reviews and Ratings
(68)Attribute Ratings
Reviews
(1-22 of 22)Microsoft Sentinel Review
- Centralized event and log data collection
- 60%6.0
- Correlation
- 50%5.0
- Event and log normalization/management
- 70%7.0
- Deployment flexibility
- 60%6.0
- Integration with Identity and Access Management Tools
- 60%6.0
- Custom dashboards and workspaces
- 50%5.0
- Log retention
- 40%4.0
- Behavioral analytics and baselining
- 50%5.0
- Rules-based and algorithmic detection thresholds
- 50%5.0
- Incident indexing/searching
- 30%3.0
Surpassingly really good tool and a very interactive dashboard
- Centralized event and log data collection
- 80%8.0
- Correlation
- 70%7.0
- Event and log normalization/management
- 80%8.0
- Deployment flexibility
- 80%8.0
- Integration with Identity and Access Management Tools
- 90%9.0
- Custom dashboards and workspaces
- 90%9.0
- Host and network-based intrusion detection
- 80%8.0
- Log retention
- 80%8.0
- Data integration/API management
- 70%7.0
- Behavioral analytics and baselining
- 80%8.0
- Rules-based and algorithmic detection thresholds
- 80%8.0
- Response orchestration and automation
- 80%8.0
- Incident indexing/searching
- 80%8.0
SIEM means Sentinel
- Centralized event and log data collection
- 90%9.0
- Correlation
- 80%8.0
- Event and log normalization/management
- 80%8.0
- Deployment flexibility
- 100%10.0
- Integration with Identity and Access Management Tools
- 90%9.0
- Custom dashboards and workspaces
- 70%7.0
- Host and network-based intrusion detection
- 60%6.0
- Log retention
- 60%6.0
- Data integration/API management
- 70%7.0
- Behavioral analytics and baselining
- 80%8.0
- Rules-based and algorithmic detection thresholds
- 90%9.0
- Response orchestration and automation
- 90%9.0
- Incident indexing/searching
- 90%9.0
Why you should start using Microsoft Sentinel today.
- Centralized event and log data collection
- 100%10.0
- Correlation
- 100%10.0
- Event and log normalization/management
- 70%7.0
- Deployment flexibility
- 80%8.0
- Integration with Identity and Access Management Tools
- 80%8.0
- Custom dashboards and workspaces
- 80%8.0
- Host and network-based intrusion detection
- N/AN/A
- Log retention
- 100%10.0
- Data integration/API management
- 80%8.0
- Behavioral analytics and baselining
- N/AN/A
- Rules-based and algorithmic detection thresholds
- 100%10.0
- Response orchestration and automation
- 100%10.0
- Incident indexing/searching
- 100%10.0
Sentinel: Your one stop SIEM for cloud for Bird's Eyes by MS.
- Centralized event and log data collection
- 80%8.0
- Correlation
- 70%7.0
- Event and log normalization/management
- 60%6.0
- Deployment flexibility
- 100%10.0
- Integration with Identity and Access Management Tools
- 70%7.0
- Custom dashboards and workspaces
- 50%5.0
- Host and network-based intrusion detection
- 80%8.0
- Log retention
- 80%8.0
- Data integration/API management
- 80%8.0
- Behavioral analytics and baselining
- 70%7.0
- Rules-based and algorithmic detection thresholds
- 90%9.0
- Response orchestration and automation
- 100%10.0
- Incident indexing/searching
- 70%7.0
Microsoft Sentinel, the scaleable cloud-native SIEM platform
- Centralized event and log data collection
- 80%8.0
- Correlation
- 80%8.0
- Event and log normalization/management
- 60%6.0
- Deployment flexibility
- 50%5.0
- Integration with Identity and Access Management Tools
- 80%8.0
- Custom dashboards and workspaces
- 80%8.0
- Host and network-based intrusion detection
- 50%5.0
- Log retention
- 70%7.0
- Data integration/API management
- 80%8.0
- Behavioral analytics and baselining
- 80%8.0
- Rules-based and algorithmic detection thresholds
- 70%7.0
- Response orchestration and automation
- 60%6.0
- Incident indexing/searching
- 90%9.0
- Centralized event and log data collection
- 80%8.0
- Correlation
- 70%7.0
- Event and log normalization/management
- 80%8.0
- Deployment flexibility
- 90%9.0
- Integration with Identity and Access Management Tools
- 80%8.0
- Custom dashboards and workspaces
- 90%9.0
- Host and network-based intrusion detection
- 80%8.0
- Log retention
- 80%8.0
- Data integration/API management
- 80%8.0
- Behavioral analytics and baselining
- 80%8.0
- Rules-based and algorithmic detection thresholds
- 70%7.0
- Response orchestration and automation
- 80%8.0
- Incident indexing/searching
- 90%9.0
Review of Microsoft Sentinel
- Centralized event and log data collection
- 80%8.0
- Correlation
- 80%8.0
- Event and log normalization/management
- 70%7.0
- Deployment flexibility
- 70%7.0
- Integration with Identity and Access Management Tools
- 70%7.0
- Custom dashboards and workspaces
- 80%8.0
- Host and network-based intrusion detection
- 80%8.0
- Log retention
- 70%7.0
- Data integration/API management
- 80%8.0
- Behavioral analytics and baselining
- 80%8.0
- Rules-based and algorithmic detection thresholds
- 80%8.0
- Response orchestration and automation
- 90%9.0
- Incident indexing/searching
- 80%8.0
One stop solution for all security needs. Transforming Security with AI and Automation
- Centralized event and log data collection
- 80%8.0
- Correlation
- 70%7.0
- Event and log normalization/management
- 70%7.0
- Custom dashboards and workspaces
- 80%8.0
- Host and network-based intrusion detection
- 70%7.0
- Log retention
- 70%7.0
- Data integration/API management
- 70%7.0
- Response orchestration and automation
- 80%8.0
- Incident indexing/searching
- 70%7.0
Excellent cloud security solution with intelligent analytics and automation offered by Microsoft.
- Centralized event and log data collection
- 90%9.0
- Correlation
- 80%8.0
- Event and log normalization/management
- 90%9.0
- Deployment flexibility
- 90%9.0
- Integration with Identity and Access Management Tools
- 80%8.0
- Custom dashboards and workspaces
- 80%8.0
- Host and network-based intrusion detection
- 90%9.0
- Log retention
- 80%8.0
- Data integration/API management
- 90%9.0
- Behavioral analytics and baselining
- 90%9.0
- Rules-based and algorithmic detection thresholds
- 80%8.0
- Response orchestration and automation
- 80%8.0
- Incident indexing/searching
- 90%9.0
A big SIEM or a little SOAR?
- Centralized event and log data collection
- 80%8.0
- Correlation
- 100%10.0
- Event and log normalization/management
- 80%8.0
- Deployment flexibility
- 90%9.0
- Integration with Identity and Access Management Tools
- 80%8.0
- Custom dashboards and workspaces
- 60%6.0
- Host and network-based intrusion detection
- 70%7.0
- Log retention
- 90%9.0
- Data integration/API management
- 90%9.0
- Behavioral analytics and baselining
- 100%10.0
- Rules-based and algorithmic detection thresholds
- 90%9.0
- Response orchestration and automation
- 80%8.0
- Incident indexing/searching
- 90%9.0
Microsoft Sentinel Review
- Centralized event and log data collection
- N/AN/A
- Correlation
- N/AN/A
- Event and log normalization/management
- N/AN/A
- Deployment flexibility
- N/AN/A
- Integration with Identity and Access Management Tools
- N/AN/A
- Custom dashboards and workspaces
- N/AN/A
- Host and network-based intrusion detection
- N/AN/A
- Log retention
- N/AN/A
- Data integration/API management
- N/AN/A
- Behavioral analytics and baselining
- N/AN/A
- Rules-based and algorithmic detection thresholds
- N/AN/A
- Response orchestration and automation
- N/AN/A
- Incident indexing/searching
- N/AN/A
Microsoft Sentinel Review
- Centralized event and log data collection
- N/AN/A
- Correlation
- N/AN/A
- Event and log normalization/management
- N/AN/A
- Deployment flexibility
- N/AN/A
- Integration with Identity and Access Management Tools
- N/AN/A
- Custom dashboards and workspaces
- N/AN/A
- Host and network-based intrusion detection
- N/AN/A
- Log retention
- N/AN/A
- Data integration/API management
- N/AN/A
- Behavioral analytics and baselining
- N/AN/A
- Rules-based and algorithmic detection thresholds
- N/AN/A
- Response orchestration and automation
- N/AN/A
- Incident indexing/searching
- N/AN/A
Microsoft Sentinel Review
- Centralized event and log data collection
- N/AN/A
- Correlation
- N/AN/A
- Event and log normalization/management
- N/AN/A
- Deployment flexibility
- N/AN/A
- Integration with Identity and Access Management Tools
- N/AN/A
- Custom dashboards and workspaces
- N/AN/A
- Host and network-based intrusion detection
- N/AN/A
- Log retention
- N/AN/A
- Data integration/API management
- N/AN/A
- Behavioral analytics and baselining
- N/AN/A
- Rules-based and algorithmic detection thresholds
- N/AN/A
- Response orchestration and automation
- N/AN/A
- Incident indexing/searching
- N/AN/A
Microsoft Sentinel Review
- Centralized event and log data collection
- N/AN/A
- Correlation
- N/AN/A
- Event and log normalization/management
- N/AN/A
- Deployment flexibility
- N/AN/A
- Integration with Identity and Access Management Tools
- N/AN/A
- Custom dashboards and workspaces
- N/AN/A
- Host and network-based intrusion detection
- N/AN/A
- Log retention
- N/AN/A
- Data integration/API management
- N/AN/A
- Behavioral analytics and baselining
- N/AN/A
- Rules-based and algorithmic detection thresholds
- N/AN/A
- Response orchestration and automation
- N/AN/A
- Incident indexing/searching
- N/AN/A
Microsoft Sentinel
- Centralized event and log data collection
- N/AN/A
- Correlation
- N/AN/A
- Event and log normalization/management
- N/AN/A
- Deployment flexibility
- N/AN/A
- Integration with Identity and Access Management Tools
- N/AN/A
- Custom dashboards and workspaces
- N/AN/A
- Host and network-based intrusion detection
- N/AN/A
- Log retention
- N/AN/A
- Data integration/API management
- N/AN/A
- Behavioral analytics and baselining
- N/AN/A
- Rules-based and algorithmic detection thresholds
- N/AN/A
- Response orchestration and automation
- N/AN/A
- Incident indexing/searching
- N/AN/A
Microsoft Sentinel Review
- Centralized event and log data collection
- N/AN/A
- Correlation
- N/AN/A
- Event and log normalization/management
- N/AN/A
- Deployment flexibility
- N/AN/A
- Integration with Identity and Access Management Tools
- N/AN/A
- Custom dashboards and workspaces
- N/AN/A
- Host and network-based intrusion detection
- N/AN/A
- Log retention
- N/AN/A
- Data integration/API management
- N/AN/A
- Behavioral analytics and baselining
- N/AN/A
- Rules-based and algorithmic detection thresholds
- N/AN/A
- Response orchestration and automation
- N/AN/A
- Incident indexing/searching
- N/AN/A
Microsoft Sentinel Review
- Centralized event and log data collection
- N/AN/A
- Correlation
- N/AN/A
- Event and log normalization/management
- N/AN/A
- Deployment flexibility
- N/AN/A
- Integration with Identity and Access Management Tools
- N/AN/A
- Custom dashboards and workspaces
- N/AN/A
- Host and network-based intrusion detection
- N/AN/A
- Log retention
- N/AN/A
- Data integration/API management
- N/AN/A
- Behavioral analytics and baselining
- N/AN/A
- Rules-based and algorithmic detection thresholds
- N/AN/A
- Response orchestration and automation
- N/AN/A
- Incident indexing/searching
- N/AN/A
- Centralized event and log data collection
- 90%9.0
- Correlation
- 90%9.0
- Event and log normalization/management
- 90%9.0
- Deployment flexibility
- 90%9.0
- Integration with Identity and Access Management Tools
- 90%9.0
- Custom dashboards and workspaces
- 80%8.0
- Host and network-based intrusion detection
- 90%9.0
- Log retention
- 80%8.0
- Data integration/API management
- 90%9.0
- Behavioral analytics and baselining
- 80%8.0
- Rules-based and algorithmic detection thresholds
- 80%8.0
- Response orchestration and automation
- 90%9.0
- Reporting and compliance management
- 90%9.0
- Incident indexing/searching
- 90%9.0
Sentinel Has Come A Long Way
- Centralized event and log data collection
- 100%10.0
- Correlation
- 100%10.0
- Event and log normalization/management
- 90%9.0
- Deployment flexibility
- 60%6.0
- Integration with Identity and Access Management Tools
- 100%10.0
- Custom dashboards and workspaces
- 80%8.0
- Host and network-based intrusion detection
- 80%8.0
- Log retention
- 90%9.0
- Data integration/API management
- 90%9.0
- Behavioral analytics and baselining
- 90%9.0
- Rules-based and algorithmic detection thresholds
- 90%9.0
- Response orchestration and automation
- 90%9.0
- Reporting and compliance management
- 90%9.0
- Incident indexing/searching
- 90%9.0
- Centralized event and log data collection
- 100%10.0
- Correlation
- 90%9.0
- Event and log normalization/management
- 100%10.0
- Deployment flexibility
- 100%10.0
- Integration with Identity and Access Management Tools
- 90%9.0
- Custom dashboards and workspaces
- 100%10.0
- Host and network-based intrusion detection
- 100%10.0
- Log retention
- 90%9.0
- Data integration/API management
- 100%10.0
- Behavioral analytics and baselining
- 90%9.0
- Rules-based and algorithmic detection thresholds
- 100%10.0
- Response orchestration and automation
- 100%10.0
- Reporting and compliance management
- 100%10.0
- Incident indexing/searching
- 90%9.0
- Centralized event and log data collection
- 100%10.0
- Correlation
- 90%9.0
- Event and log normalization/management
- 100%10.0
- Deployment flexibility
- 90%9.0
- Integration with Identity and Access Management Tools
- 100%10.0
- Custom dashboards and workspaces
- 100%10.0
- Host and network-based intrusion detection
- 90%9.0
- Log retention
- 100%10.0
- Data integration/API management
- 100%10.0
- Behavioral analytics and baselining
- 100%10.0
- Rules-based and algorithmic detection thresholds
- 100%10.0
- Response orchestration and automation
- 100%10.0
- Reporting and compliance management
- 100%10.0
- Incident indexing/searching
- 100%10.0