Infocyte HUNT vs. Trellix Automated Response
Infocyte HUNT vs. Trellix Automated Response
| Product | Rating | Most Used By | Product Summary | Starting Price |
|---|---|---|---|---|
 Infocyte HUNT | N/A | Infocyte HUNT aims to provide an easy-to-use, yet powerful enterprise endpoint security solution. Infocyte HUNT is a threat hunting software/platform designed to limit risk and eliminate dwell time by enabling an organization’s own IT and security professionals to proactively discover malware and persistent threats, active or dormant, that have successfully breached existing defenses. According to the vendor, Infocyte HUNT uses a forensic… | N/A | |
 Trellix Automated Response | N/A | Security orchestration and automation helps users improve response times, reduce risk exposure and maintain process consistency across a security program. Being able to simplify security operations means being able to prioritize alerts, improve staff efficiencies and decrease response times. Trellix Automated Response is a solution designed to provide this. | N/A |
| Infocyte HUNT | Trellix Automated Response | |||||||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| Editions & Modules | No answers on this topic | No answers on this topic | ||||||||||||||
| Offerings |
| |||||||||||||||
| Entry-level Setup Fee | Optional | No setup fee | ||||||||||||||
| Additional Details | — | — | ||||||||||||||
| More Pricing Information | ||||||||||||||||
| Infocyte HUNT | Trellix Automated Response | |
|---|---|---|
| Small Businesses |  NinjaOne Score 9.2 out of 10 | No answers on this topic |
| Medium-sized Companies |  Nmap Score 8.9 out of 10 |  Splunk SOAR Score 8.2 out of 10 |
| Enterprises |  Nmap Score 8.9 out of 10 |  Palo Alto Networks Cortex XSOAR Score 8.5 out of 10 |
| All Alternatives | View all alternatives | View all alternatives |
| Infocyte HUNT | Trellix Automated Response | |
|---|---|---|
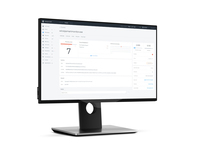
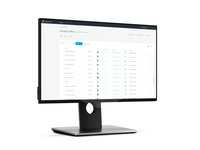
| ScreenShots | Infocyte HUNT Screenshots |